Lokesh Kumar, a security analyst at InfySEC Demystify about QRL Jacking in oct 11,2019
Nithin's Article on DeepFakes covered on International PenTest Mag. He said that hackers have always been the types of people who have harnessed any technology out there in the wild to gain an edge. It is not surprising that attackers have managed to find a way to weaponize machine learning to exploit our natural tendency to trust that what we see is real
InfySEC consulting team conducted a Cybersecurity research demo on UAC forcing and C&C channeling via Dropbox
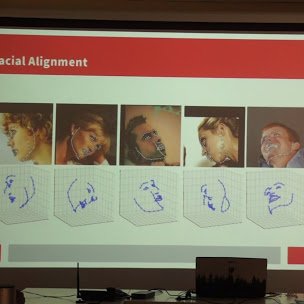
InfySEC consulting team conducted a Cybersecurity research demo on Deepfaking
InfySEC consulting team conducted a demo on QRL jacking
Presentation on Advanced Cyber Attacks held on 10 Sep- 17 Sep. Topics covered:
1. QRL Jacking - Lokesh
2. Remote Harvest login via UAC force - Jebaraj
3. DeepFakes - Voice and Video - Nithin



.jpg)